Design of a private cloud solution based on a distributed monitoring algorithm: Application to IaaS services.
Introduction
Information technologies are changing and revolutionizing the way people live and work. Cloud computing has emerged in recent years as a new model of administration and use of computing resources. According to the National Institute of Standard and Technology, cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources that can be rapidly provisioned and released with minimal management effort or provider interaction. For IBM, it is both a new computing working mode, whereby data, applications and computing resources are dynamically made available to users; and an administration mode which allows the management of a large number of virtualized resources that can be installed on multiple sites in order to present them as unique. This introduces many advantages such as a great degree of flexibility, a simplified way for computing resources sharing, etc. Several cloud solutions, either from proprietary public or open-source private cloud, have then been developed in order to facilitate access to this new economical computing model. Then, it is critical these solutions meet security, fault-tolerance and high availability issues. About the public cloud solution, security issues (Subashini and Kavitha, 2011) and vendor lock-in (Galán et al, 2009) are the main obstacles limiting their adoption. Concerning the private cloud solutions, Nurmi et al (2008), Sempolinski and Thain (2010), and Alrwais, (2011) show that all current solutions are based on centralized monitoring architectures, which may result in the breaking of the services in case of failure of the system’s central node (Naing, 2012). Then, in order to contribute to solve this problem, and help computer engineering and maintenance companies such as Logisoft-Bénin to have high available and fault-tolerant private cloud architecture for internal use, we have proposed a new private cloud solution using a distributed monitoring algorithm. This summary intended to present our work is structured into three parts: firstly we will present the cloud computing architectures and current available solutions. Then we will go through its enabling technologies. The third part will present our solution with the materials and method used to implement it.
1. Background of Cloud computing
A cloud can either be public, private or for a community. The combination of private and public cloud is called hybrid cloud. All the different types of cloud computing deliver essentially three services which are Infrastructure as a service (IaaS), Platform as a service PaaS and Software as a service (SaaS). IaaS layer provides cloud consumers with IT (Information Technology) Infrastructure such as (processing, storage, networks and other fundamental computing resources). The PaaS level is made of a set of tools that provide full development and execution platforms for cloud users. The higher level (SaaS) provides software and applications to end-users. 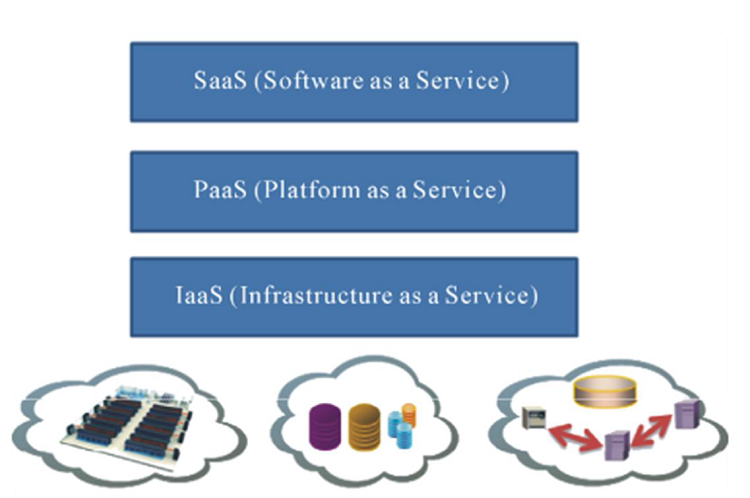
Figure 1.1: Layers of cloud computing architecture.
1.1. Public Cloud computing
The public cloud is where the service is delivered by a third-party cloud provider to private enterprises or individuals. This allows cloud consumers to leave the administration of their computing systems to external providers. It introduces many advantages such as great mobility and high availability of resources accessed through Internet on-demand and in devices independent manner. The main actors in the public cloud domain are Google with its App Engine PaaS services, Microsoft with its Azure PaaS platform and Amazon with its Elastic Compute Cloud (EC2) IaaS services. Others actors included Salesforce deliver both PaaS and SaaS services.
1.2. Private Cloud computing
Private cloud allows enterprises to internally deploy the architecture for personal use. The virtualization technologies used in cloud computing makes it possible to get better management of available resources. Private cloud is typically of great interest for large companies or universities. For the universities, it is used to provide students with computing resources for test and e-learning activities through dynamic virtual machine attribution. Projects such as VCL (Virtual Computing Laboratory) of the North Carolina State University and CloudIA (Cloud Infrastructure and Application) of Hochschule Furtwangen University (HFU) show concrete implementations of private cloud for e-learning. Private cloud generally deals with IaaS services implementation. Sun et al (2011) provides an overview of the different components of theses services’ enabling architecture. The system is made of three major components: the administration center that allows users to access resources through a Web portal by using protocol such as VNC, RDP or SSH, the cloud resources center providing physical resources to be used as host nodes for the users’ virtual machines and finally the cloud storage resource center which is composed by the physical storage resources used to host the virtual machines templates which are transferred to the cloud resource center when creating new virtual machines for users. 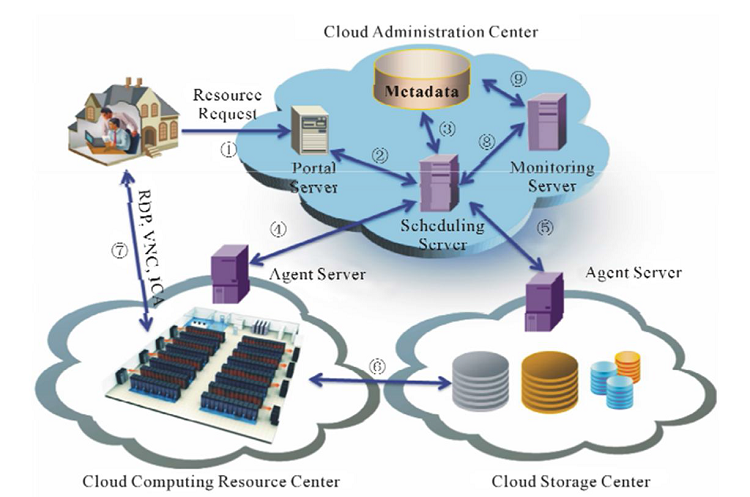
Figure 1.2: Infrastructure as a service (IaaS) components.
For Infrastructure as a Service private cloud platforms purpose, there are several open-source existing solutions (Eucalyptus, OpenNebula, OpenStack, Nimbus, etc.) which provide the system as common software to deploy and use. A key common point to all these solutions is the centralized monitoring architecture needed to deliver services. Eucalyptus cloud based architecture shows the actual centralization of private cloud system (Figure 1.2). The solution includes three essentials nodes for the monitoring of the services: the cloud controller (CLC), the cluster controller CC and the node controller NC. The CLC is the central node of the architecture. It monitors the system through the different CC on the network. Cluster controllers are the intermediary nodes used by the CLC to collect information over the entire network. Each CC is in charge of a number of node controllers. The role of the different NCs is to monitor the single physical computing node on which they are installed. The other components of the system deal with the management of users’ data and the security concerns. Eucalyptus architecture is seemingly encountered in the other private cloud solutions such as OpenNebula where the save terms namely cluster, node or cloud controller are used. 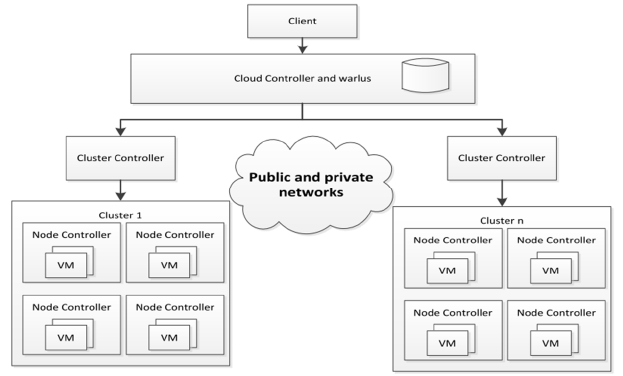
Figure 1.3: Eucalyptus Architecture.
2. Enabling cloud computing technologies
The main technologies that contribute to cloud computing solutions are: virtualization and Web technologies.
2.1. Virtualization
Virtualization is concerned with all techniques used to run multiple operating systems on a single physical machine. It provides resources needed to support cloud applications. It is critical for Infrastructure as a Service implementation. Many solutions such as Xen, KVM, VMware or Hyper-V allow the use of virtualization through different technologies: full virtualization, para-virtualization and the hypervisor system. The virtualization offers many advantages such as virtual machine migration which consists of transferring a virtual machine files from a physical host to a destination host. The most used and open source virtualization solution is Xen. Xen is a Virtual Machine Monitor (VMM) also known as a hypervisor. It is a software system that allows the execution of multiple virtual guest operating systems simultaneously on a single physical machine.
2.2. Web services
Cloud computing services are normally exposed to the end-users as Web services following the industry standards such as WSDL (Web Services Description Language), UDDI (Universal Description Discovery and Integration). Moreover, internal cloud components inter-communication is made possible using Web service technologies such as XML-RPC (Extensible Markup Language), REST (Representational State Transfer) or SOAP (Simple Object Access Protocol).
3. Materials and methods
3.1. Methods
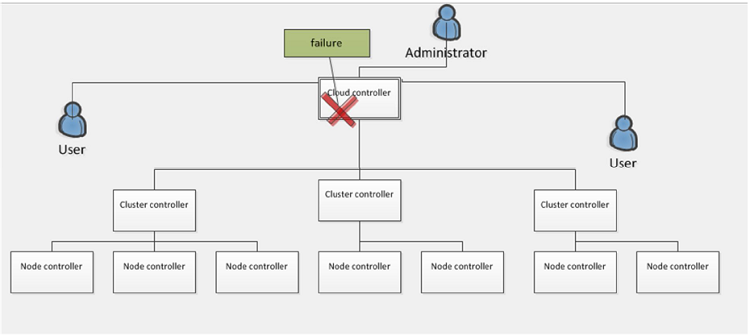
Current private cloud solutions architectures are centralized. Most of them use a tree representation of the different nodes on the network in which a single head-node, namely the CLC, takes the entire advantage to monitor all the system. This way, an occurring failure at this node should result in a breaking of the services rendered to the cloud consumers. This should also block the actual monitoring services performed by the CLC.
Figure 3.1: CLC failure.
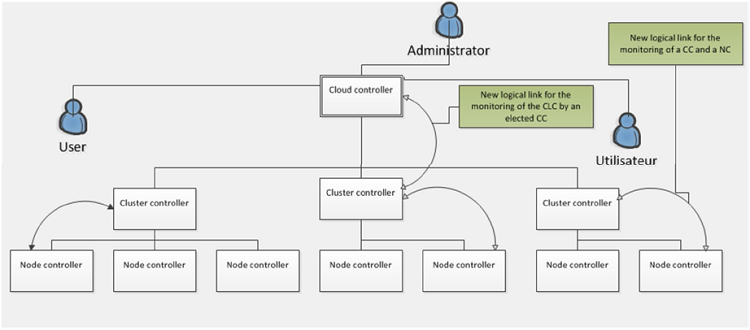
The same problem occurs at any cluster controller where access to the information of this cluster by the cloud controller should become impossible in case of a failure of that cluster controller. One of the solutions to solve this problem is to elect one CC from among the different CCs on the network of which the role will consist in overseeing the current CLC. The same technique should also be applied to each cluster of the system where a node controller should be elected to supervise the actual leader of that cluster. Then, when the cloud controller, eventually, will come to fail, the elected CC node would detect this failure and changes its own state to get in charge of the functions of the lost CLC. Similarly, in each cluster, the elected node controller (NC) will be called to get in charge of the role of its leader when this later node will come to fail.
Figure 3.2: The proposed solution.
3.2. Modeling our solution
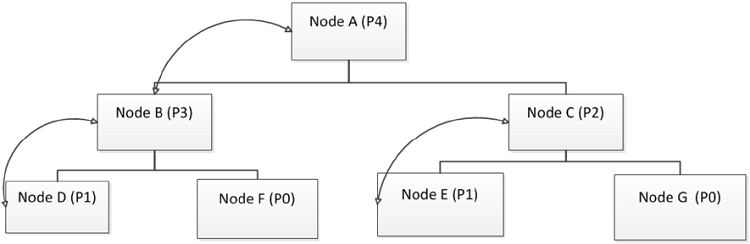
The election scheme proposed in our solution is performed by using five privileges values ranged from 0, 1, 2, 3 to 4. The running process on each physical node on the network should then have five distinct states. A node holding 0 privilege value should act as a simple node controller. Its role will consist in monitoring the single physical node on which it is executed. The privilege 0 state is also the default starting state of all the different nodes. When a node is elected by a CC, it should be affected the value 1 as its privilege value. All the CCs on the network should hold the value 2 of privilege. When a CC is elected by the cloud controller, it should be affected the value 3. The privilege value of the cloud controller should be fixed at 4. At the starting of the system, all the different nodes should hold the value 0 as their default privilege value. Then an initial node should be selected to perform the registering process. This will consist in adding other nodes to the system. Adding a first node to the initial selected node should make its state transit from 0 to 4. The first node added should be affected the value 3. This node will be registered by the CLC as a leader of a new created cluster. From this moment, adding a node as a new cluster leader to the system should result in affecting the value 2 to this node by the actual CLC. Moreover, adding a first node to a cluster, having already a leader, should result in attributing the value 1 to that node. A new node added to a cluster having already a leader and an elected node should result in attributing the value 0 to that node. We use Pi to represent a process holding a privilege i value on a node (Figure 3.1).
Figure 3.3: Registering process of the proposed solution.
After the initialization process, each node of the system should work using its privilege value. When a CLC failure occurs, the elected CC will dynamically modify its privilege value from 3 to 4 making it transit from CC to CLC state. This process will result in the election of a new CC from among the remaining CCs on the network. When a CC failure occurs, the elected NC will dynamically change its privilege value from 1 to 2 making it transit from NC to CC state. This later process will also result in the election of a new NC from among the remaining NCs of that cluster.
3.3. Technical choices
Our proposal represents a new solution for private cloud implementation. Its main objective is to take into account the fault-tolerance in the system for the high availability of IaaS services. To achieve this, we have made the following choices : – The system’s components inter-communication protocol : XML-RPC – The virtualization solution: Xen – Programming languages: Java & JEE. – Operating system: Linux/Debian squeeze.
3.4. Results and discussion
The implementation of our solution lead to the development of two applications: a distributed application written in java for the monitoring of services and a Web application for the administration and the use of IaaS services. In order to test the ability of our solution to ensure high availability and fault-tolerance in a private cloud environment, we have executed the application on three host nodes and executed our Web application inside a virtual machine created using Xen. This Virtual machine is held by the initial node selected as CLC and the other two nodes are added to the system as cluster controllers. The first node added to the system has been affected the value 3 as its privilege value and the second node has got 2 as its privilege value. Then the virtual machine hold by the actual cloud controller has been replicated on the elected cluster controller node. When we suddenly removed the CLC from the Ethernet switch used to establish the private network, the elected CC automatically changed its state by modifying its value from 3 to 4, then started the virtual machine hosting the Web application and finally elected the remaining node on the network as the new elected CC node. Our system is different from the other private cloud solutions. It is based on a distributed monitoring algorithm which provides it with the ability to dynamically reconfigure itself for the services continuity. Naing (2012) proposed a similar solution through a fault-tolerance management framework that allows a dynamical rebuilding of certain critical nodes of the system. Her solution needs to replicate the central node information at least three times. Moreover, it is based on Eucalyptus which is a centralized monitoring architecture based solution. Our solution, on the other hand, is a fully-fledged private cloud solution that naturally supports fault-tolerance features for the high availability of Infrastructure services. To ensure high availability, our solution uses virtual machine migration through the secure shell (SSH) protocol. This latter feature requires all the host nodes of the system to have a minimum disk space in order to receive and run the migrated virtual machine. Moreover, the solution supports the administration of physical and virtual machines through a command line interface (CLI) and a web portal. It also includes a VNC (virtual network protocol) client allowing access to the cloud machines through the Web application. This interface offers much more flexibility to use the system. The solution also allows users accounts creation with the ability to assign them a number of virtual machines. It is compatible with Xen virtualization system and offers the possibilities to deploy, to start and to stop created virtual machines.
Conclusion
In this work, we have proposed a new private cloud solution based on a distributed monitoring algorithm. This algorithm makes it possible to ensure high availability of IaaS services. It supports fault-tolerance and allows the continuity of the services in case of any node failure. However, its infancy in the domain of cloud computing requires important effort to make for its evolution.